FAQ for Participating Institutions/Administrators
- How does eduroam work?
- What technology does eduroam use?
- What is eduroam South Africa's architecture?
- Is eduroam safe to use?
- Can eduroam use a captive portal?
- Does eduroam work on different platforms?
- Are there any prerequisites for eduroam?
- Can we use eduroam as our only Wi-Fi network?
- Can anyone help us deploy eduroam?
- How do we get started with eduroam?
- Managing eduroam services
- Monitoring and testing your eduroam IdP or SP
- Additional information
How does eduroam work?
The idea of eduroam is to leave the administration of user accounts to the entity that a user comes from. All the sites participating in eduroam all over the world are linked by a hierarchy of RADIUS servers.
If one of your users visits a participating eduroam institution site, then that site will ask your RADIUS server to authenticate the visiting user. If your RADIUS server is configured to be OK with the visiting user, then the remote site will also allow your visiting user to use the remote site's Internet connection — no VPNs are configured.
If your campus gets a visitor from another participating eduroam site, e.g. from the CSIR, then your RADIUS server will ask the CSIR's RADIUS server to authenticate the visitor. If the CSIR's RADIUS server is OK with that user, then you will allow that user to use your Internet connection (usually just outside your firewall). This process is summarised for a student at the hypothetical MyUni university in the animation below:
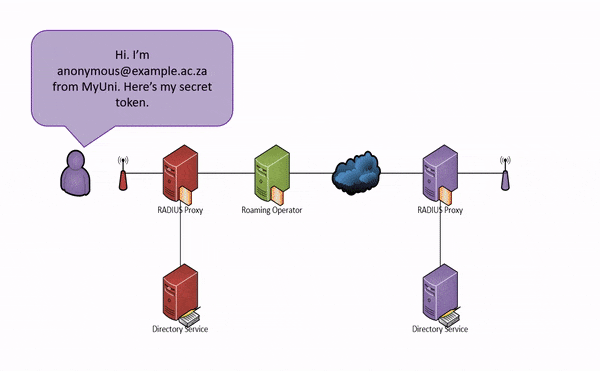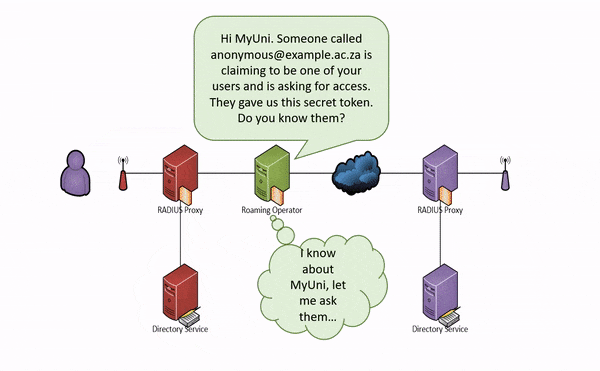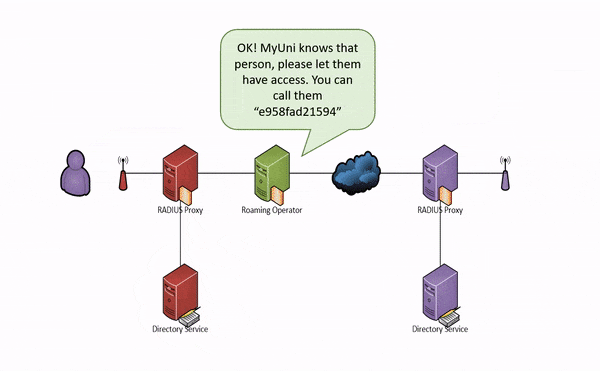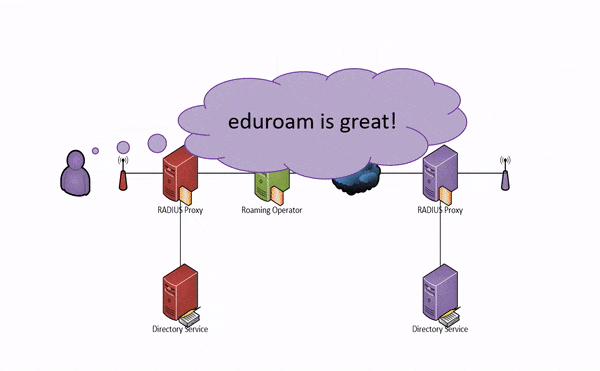
Note that neither the visited institution (the service provider) nor the national roaming operator needs to know who the user is; only where they are from. This is because all the necessary routing information (anonymous@example.ac.za above) is carried in the unencrypted outer identity whereas authentication information (Bob) need only be carried in the encrypted inner identity. This is good for protecting the privacy of users and reduces the amount of personal information the SP needs to handle (think POPI). However, eduroam is not anonymous — together the SP, IdP and NRO can work together to establish the real identity of a user, and this cooperation is required in certain circumstances (e.g. when requested by a law enforcement agency).
For more information see: www.eduroam.org
What technology does eduroam use?
In eduroam, communication between the access point and the user's home institution is based on IEEE 802.1x standard; 802.1x encompasses the use of the Extensible Authentication Protocol (EAP), which allows for different authentication methods.
The two most popular EAP methods being used by eduroam is EAP-TTLS and EAP-PEAP. A secure tunnel will be established from the user’s computer to his home institution through which the actual authentication information (username/password etc.) will be carried.
What is eduroam South Africa's architecture?
South Africa's eduroam architecture is shown in the diagram below:
As you can see there are four instances of the public facing FLR RADIUS proxies, of which only two are normally active. These correspond to flr-jnb.eduroam.ac.za and flr-cpt.eduroam.ac.za, being the RADIUS servers you configure in your own RADIUS configs. The intent is to create a scalable, resilient architecture capable of handling hundreds of thousands of authentications a day.
If your RADIUS server does not load balance, please choose the FLR server that's geographically closer to you as the primary one.
Is eduroam safe to use?
eduroam is based on the most secure encryption and authentication standards in existence today. Its security by far exceeds typical commercial hotspots. Be aware though that when your users are using the general Internet at an eduroam hotspot, the local site security measures at that hotspot will apply to them as well. For example, the firewall settings at the visited place may be different from those they are used to at home, and as a guest of the visiting institution, they may have access to fewer services on the Internet than they are used to having at home.
Can eduroam use a captive portal?
No. A Web Portal, Captive Portal or Splash-Screen based authentication mechanism is not a secure way of accepting eduroam credentials, even if the website is protected by an HTTPS secure connection. The distributed nature of eduroam would mean that many different pages, languages and layouts would be presented to eduroam users making it impossible to distinguish between legitimate and bogus sites (even a consistent layout can be mimicked by an adversary).
eduroam requires the use of 802.1x which provides end-to-end encryption to ensure that your private user credentials are only available to your home institution. The certificate of your home institution is the only point you need to trust regardless of who operates any intermediate infrastructure. Web portals require you to trust their infrastructure as they receive your password in clear text, this breaks the end-to-end encryption policy of eduroam.
Does eduroam work on different platforms?
eduroam uses open standards to enable cross-platform uniform access. This means that eduroam works on Windows, Linux, BSD, MAC OS, Android, and even Windows CE.
Are there any prerequisites for eduroam?
In order to enable your users to access eduroam on your campus, you need to maintain an Identity Management System (IdMs), where your users' electronic identities are stored. Typically this is a directory system such as LDAP, eDirectory, or Active Directory.
You also need a RADIUS server, which will have to be connected to your identity management system.
Your WiFi network must be configured to use WPA2 security in enterprise mode. You should not use WPA or WPA+WPA2 mixed mode, nor should you use TKIP encryption. Information about eduroam's compatibility with WPA3 is also available.
Can we use eduroam as our only Wi-Fi network?
Yes, you can. In fact, you probably should. Using eduroam as your only Wi-Fi network is considered best practice because it helps in several ways.
It means your users configure and test eduroam while they're on your campus. When things go wrong, they have access to your normal Help Desk structures, rather than trying to contact someone from afar, potentially in a different timezone. They can bring their device in, and you'll know it's working properly.
As all your users will have their devices pre-configured, it also means they make better use of eduroam when roaming. A student who has to configure eduroam separately to on-campus Wi-Fi is less likely to do so, meaning they loose out on opportunities to use eduroam off-campus.
We have separate document that gives advice on how to manage a migration to an eduroam-only campus.
Can anyone help us deploy eduroam?
There are a handful of network consulting companies in South Africa that have gained experience deploying and supporting eduroam at local institutions. We maintain a list.
How do we get started with eduroam?
We've created a separate page detailing the configurations required for eduroam. We also document the certificate requirements.
Managing eduroam services
IdP (Identity Provider)
In order to become an eduroam IdP, you generally also have to provide an eduroam SP service (there is an expectation of reciprocity). As an eduroam IdP, you are responsible for your own users. You should provide all the information and support for your own users to get connected to eduroam. Advise your users to test eduroam at your own campus before they visit other eduroam enabled sites.
If a user can use eduroam on your own campus then the same configuration should also work at any eduroam enabled site. To avoid configuration issues you should make use of the eduroam Configuration Assistance Tool (CAT). See: https://cat.eduroam.org/
The CAT tool gets the information about institutions from the Roaming Operators (RO) of the different NRENs. The South African RO will submit all the institutions that are registered on the SA eduroam website. As an administrator, you need to register and manage your institution on the SA eduroam website, under the manage tab above. You can then self-provision for CAT.
An IdP should keep authentication logs for a recommended period of at least six months. If one of your own users is experiencing problems at another site then they should contact you to help them. You should do the following:
- Verify the user's configuration and find out if eduroam worked before they left.
- Check on monitor.eduroam.ac.za that your realm is working from outside your network.
- Analyse your own logs first. Your RADIUS server should receive an authentication request for the user from the National eduroam servers. Remember an invalid domain e.g. koos@example.ac.za instead of koos@example.ac.za will cause the requests to be dropped along the way.
- If you don't receive the requests, then you should contact the RO operator to assist with the debugging. The following info will assist the RO in debugging:
- The login name of the user. E.g. koos@example.ac.za
- The name of the remote institution being visited and the domain they are using. e.g uct.ac.za
- Is eduroam working for other users at the remote site? IP address of one of those users.
- If the RO does not see the requests on the national eduroam servers, then the RADIUS logs from the remote administrator might be useful to track down the problem. The contact details of the other eduroam administrators should be visible after you login as an administrator on the eduroam website.
SP (Service Provider)
Any entity with an Internet connection can become an eduroam SP and as a general rule, any IdP should also be an SP. A service provider should be configured with an SSID called "eduroam" with "WPA2 Enterprise" user authentication and AES+CCMP encryption (WPA1 and TKIP are insecure and should not be used) that is connected to the national eduroam servers of the NRO. It is normal practice to separate traffic from your own users and that of eduroam visitors.
Please read through the national eduroam policy documents to see what rules an SP should comply with e.g. no portals, minimum service for visitor etc. The best way to ensure your SP is up and running is to let your own users use eduroam as well.
Monitoring and testing your eduroam IdP or SP
Separate pages exist for our monitoring service and on testing your eduroam IdP or SP.
Additional information
The GÉANT eduroam cookbook contains a lot of useful information.
